Contact
 +49-9131-85-27775
 +49-9131-85-27270
Secretary
| Monday | 8:00 - 12:15 |
| Tuesday | 8:00 - 16:45 |
| Wednesday | 8:00 - 16:45 |
| Thursday | 8:00 - 16:45 |
| Friday | 8:00 - 12:15 |
Address
Friedrich-Alexander-Universität Erlangen-Nürnberg (FAU)
Lehrstuhl für Informatik 5 (Mustererkennung)
Martensstr. 3
91058 Erlangen
Germany
Powered by

|
Image Forensics
The goal of blind image forensics is to assess authenticity and origin of digital images without an embedded security scheme. Within this field, three directions can be distinguished to reach this goal. - Verification of expected artifacts introduced in the process of image sensing
Particular camera or lens properties are exploited and checked for inconsistensies. Particular examples are the detection of lateral chromatic aberration (by M. Johnson and H. Farid) or the extraction of a characteristic sensor noise pattern (by M. Chen, J. Fridrich, M. Goljan and J. Lukas). - Detection of inconsistensies in the statistics of the output image
Successful methods are tests on JPEG artifacts (e.g. by J. He, Z. Lin and X. Tang), tests on resampling artifacts (e.g. by A. Popescu and H. Farid) or the detection of copy-move forgeries (e.g. by S. Bayram, H. Sencar and N. Memon). - Examination of properties in the depicted scene
The idea is that the depicted scene must satisfy particular physical properties. Particular examples are the recovery of the lighting direction (by M. Johnson and H. Farid) or the assessment of the illuminant color consistency (by C. Riess and E. Angelopoulou).
The research in our group focuses on the second and third branch. Recent results include - a study on the features for the detection of copy-move forgery
- the presentation of a publicly available flexible ground-truth dataset for the evaluation of output image artifacts.
- a method for the assessment of illumination color consistency
Group members in this project:  Christian Riess, Christian Riess,  Elli Angelopoulou Elli Angelopoulou
Multimedia Tools and Applications 2016, BioFor 2015
Johnson and Farid enriched image forensics with a method for estimating the lighting direction. From the 2-D contours of an object, the direction and distribution of incident light can be estimated. When we experimented with that method, we noticed that the physics-based constraints impose relatively strict constraints on the method's applicability on images in the wild. In this work, we aim to relax one of the constraints, namely the requirement that the object contour has to be selected on the same material. In our method, we allow for piecewise constant materials along the contour by incorporating an albedo correction term into the equations. The datasets for evaluation can be downloaded  here. here.
IEEE Transactions on Information Forensics and Security 2013
IEEE Transactions on Information Forensics and Security 2012
Pattern Recognition (Joint DAGM and OAGM Symposium) 2012
Workshop on Information Forensics and Security 2010
Sicherheit 2010
Example original image. | Copy-move forgery. |
We present a common pipeline for copy-move forgery detection. This formalization allows us to compare the most discriminating properties of various presented methods, their features. We perform an evaluation of ten different feature sets on a part of our benchmark database. Experiments show that the Fourier-Mellin descriptors perform outstandingly when a region is directly copied. When the copied region is additionally rotated or scaled, is PCA and DCT features were the most robust choice.
A Flexible Benchmark Database for Tampering Detection Algorithms
Information Hiding Conference 2010
|
![]() Christian Riess,
Christian Riess, ![]() Elli Angelopoulou
Elli Angelopoulou

![]() here.
here.

![]() project page. Code for creating the illuminant maps is available!
project page. Code for creating the illuminant maps is available!

![]() project page. Code and data are available!
project page. Code and data are available!


![]() project page. Code is available!
project page. Code is available!

![]() we propose the Same Affine Transform Selection (SATS) as a rotation and scale invariant extension of the popular same shift vector approach. Code is available!
we propose the Same Affine Transform Selection (SATS) as a rotation and scale invariant extension of the popular same shift vector approach. Code is available!



![]() dataset and software for large-scale evaluations of tampering artifact detection methods. The dataset consists of 48 different images together with separate tampered image parts. With use of the software, the images and the tampered parts can be freely combined, thus creating data for various realistic tampering scenarios. For instance, Gaussian and salt+pepper noise can be added, tampered parts can be scaled and rotated, as well as JPEG recompressed. We believe that it is about time for a publicly available realistic dataset for the evaluation of methods for tampering artifacts detection, especially copy-move forgery detection.
dataset and software for large-scale evaluations of tampering artifact detection methods. The dataset consists of 48 different images together with separate tampered image parts. With use of the software, the images and the tampered parts can be freely combined, thus creating data for various realistic tampering scenarios. For instance, Gaussian and salt+pepper noise can be added, tampered parts can be scaled and rotated, as well as JPEG recompressed. We believe that it is about time for a publicly available realistic dataset for the evaluation of methods for tampering artifacts detection, especially copy-move forgery detection.

![]() project page.
project page.
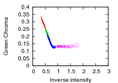
![]() In our work, we examined how to adapt illumination estimation algorithms as a cue for semantic image analysis. Most important, we focused on physics-based illumination estimation algorithms, in order to make errors in the estimation explicable. We adapted an illumination estimation method by Tan et al. Most real-world scenes consist of a mixture of specular and diffuse pixels. On such images, our algorithm yields robust results in almost real-time.
In our work, we examined how to adapt illumination estimation algorithms as a cue for semantic image analysis. Most important, we focused on physics-based illumination estimation algorithms, in order to make errors in the estimation explicable. We adapted an illumination estimation method by Tan et al. Most real-world scenes consist of a mixture of specular and diffuse pixels. On such images, our algorithm yields robust results in almost real-time.

 +49-9131-85-27775
+49-9131-85-27775
 +49-9131-85-27270
+49-9131-85-27270
